Sample DBs¶
I created this repository and the docker images so that I would always have a reference database ready to go. I find that sometimes when trying to exploit a SQL Injection vulnerability I don't know if the error I am receiving is because my exploit code syntax is incorrect or if it is an issue with the application. Now I can quickly fire up a database and test/tweak my syntax to make sure it works.
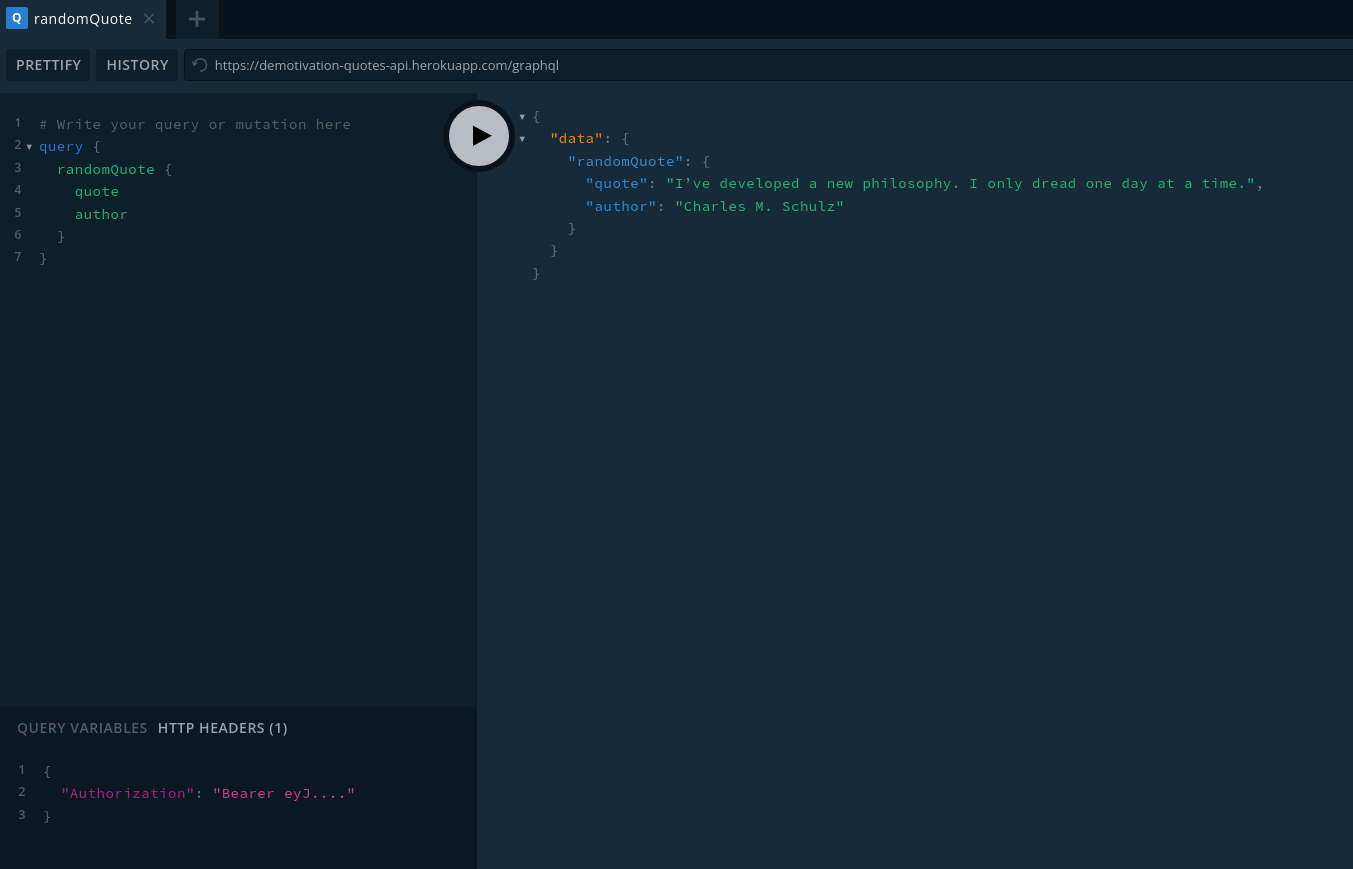
I also included the GraphQL playground to help when testing a GraphQL endpoint and want to work with an IDE of sorts.
Usage¶
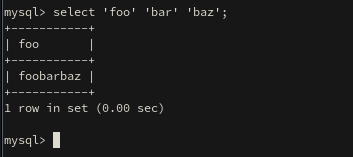
Maybe you don't remember that MySQL will concatenate quoted strings separated by spaces:
SELECT 'foo' 'bar' 'baz';
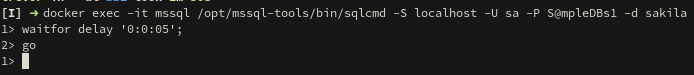
Or that MSSQL has a weird syntax for sleep:
WAITFOR DELAY '0:0:05'
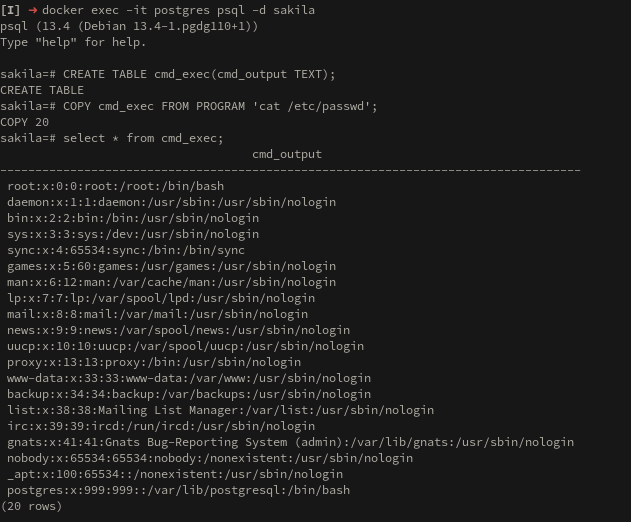
Or that PostgreSQL now allows for command execution just like the old xp_cmdshell:
CREATE TABLE cmd_exec(cmd_output TEXT);
COPY cmd_exec FROM PROGRAM 'cat /etc/passwd';
SELECT * from cmd_exec;
While these are basic examples, you can build out complicated queries to test injection against the sakila database.
GraphQL¶
Start the GraphQL container and then visit http://localhost:4000/graphql.
Now you can use this to connect to a public GraphQL endpoint. For example try connecting to: https://demotivation-quotes-api.herokuapp.com/graphql. If you need to enter in cookies, specific headers, etc... you can do so at the bottom.
query {
randomQuote {
quote
author
}
}